Vitalik's New Article: Envisioning the Ultimate Endgame of Web3, "Open Source Verifiability" to Become a Technological Norm
The security of technology and power is no longer concentrated in the hands of a few; everyone can enjoy secure and trusted digital services.
Original Article Title: The importance of full-stack openness and verifiability
Original Article Author: Vitalik Buterin
Original Article Translator: Saoirse, Foresight News
Arguably the most significant trend of this century so far can be summarized by the phrase "the internet has become real life." This trend began with email and instant messaging – private conversations that were previously conducted through oral tradition and pen-and-paper records for millennia have now moved onto digital infrastructure. Subsequently, digital finance emerged, encompassing both cryptocurrency finance and the digital transformation of traditional finance itself. Later on, digital technology penetrated the health sector: various pieces of information related to our bodies are now being processed through computers and computer networks, leveraging smartphones, personal health tracking devices, and data inferred from consumer behavior. Over the next twenty years, I anticipate this trend will sweep through more domains, including various government affairs (potentially even extending to electoral processes), monitoring of physical and biological indicators and potential threats in the public environment, and ultimately, through brain-machine interface technology, digital technology may even touch upon the cognitive aspects of our human minds.
I believe these trends are inevitable: the benefits they bring are too great, and in a fiercely competitive global environment, civilizations that reject these technologies will first lose competitiveness and eventually cede sovereignty to civilizations that embrace these technologies. However, in addition to bringing significant benefits, these technologies also profoundly impact power structures within and between nations.
The civilization that can benefit the most from a new wave of technological advancement is not the "consumer" of the technology but the "producer" of the technology. Projects designed for equal access on closed platforms and interfaces, orchestrated by a central authority, can at best realize only a small fraction of the value and often fail beyond the predefined "normal" scenarios. Furthermore, in the future technological landscape, our trust in technology will significantly increase. Once this trust is broken (e.g., through backdoors, security vulnerabilities), serious issues can arise. Even the mere "possibility" of trust being broken will force people back into fundamentally exclusive social trust patterns – namely, "Is this thing built by someone I trust?" This situation will create a chain reaction at various levels of the tech stack: the so-called "governors" are those who can define the "special cases."
To mitigate these issues, various technologies in the tech stack – including software, hardware, and biotechnologies – must possess two interrelated core features: true openness (i.e., open-source, including free licensing) and verifiability (ideally, end-users should be able to verify directly).
The Internet is now part of real life. We hope it becomes a utopia rather than a dystopia.
The Importance of Openness and Verifiability in the Health Field
During the COVID-19 pandemic, the consequences of unequal access to technological means of production were starkly revealed. Vaccines were only produced in a few countries, leading to a significant disparity in the timing of vaccine access between nations: wealthy countries obtained high-quality vaccines in 2021, while other countries only received lower-quality vaccines in 2022 or 2023. Despite various efforts at the time to ensure equitable vaccine access, the limited effect of these measures was due to vaccine production relying on capital-intensive proprietary manufacturing processes that could only be carried out in a few locations.
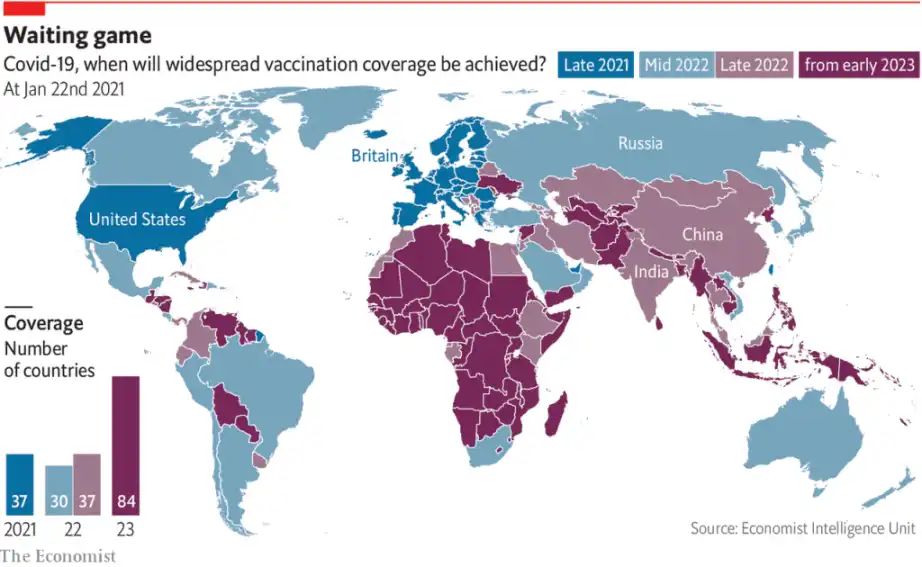
2021-2023 COVID-19 Vaccine Coverage Data
The second major issue facing vaccines is the lack of transparency in their related scientific research and information dissemination strategy: stakeholders attempted to claim to the public that the vaccine was "completely risk-free, without any side effects," a statement that was not in line with the facts, ultimately greatly exacerbating public distrust in the vaccine. Today, this distrust has escalated to the point of questioning scientific achievements of the past half-century.
In fact, both of these issues have solutions. For example, vaccines like PopVax, funded by Balvi, have lower research and development costs and greater openness in the R&D process—this can not only reduce the inequality in vaccine access but also make the analysis and verification of their safety and efficacy easier. In the future, we can even make "verifiability" a core goal in vaccine design from the outset.
Similar issues also exist in the digitalization of biotechnology field. When you talk to longevity researchers, they almost always mention that the future direction of anti-aging healthcare is "personalized" and "data-driven." To provide precise medication advice and nutrition adjustment plans for people today, it is necessary to understand their real-time bodily conditions; to achieve this, large-scale, real-time digital data collection and processing are crucial.

The amount of personal data collected by a smartwatch is 1,000 times that of Worldcoin, illustrating the pros and cons of this phenomenon.
This logic also applies to defensive biotechnology aimed at "risk prevention," such as epidemic prevention and control. The earlier an epidemic is discovered, the more likely it can be contained at the source; even if containment is not possible, every week of early detection allows more time to prepare for and develop response measures. During a continuing epidemic, having real-time information on the locations of outbreaks is also of significant value for promptly deploying prevention and control measures: if an ordinary person infected with the epidemic can self-isolate within 1 hour of becoming aware of the illness, the spread of the epidemic will be reduced by a factor of 72 compared to the scenario of "carrying the illness for 3 days and infecting others"; if it can be determined that "20% of locations account for 80% of the transmission," improving the air quality in these areas can further reduce the transmission risk. To achieve these goals, two conditions must be met: (1) deploying a large number of sensors; (2) sensors must have real-time communication capabilities to provide feedback to other systems.
Looking further into the "sci-fi level" technological direction, we can see the potential of brain-machine interfaces—it can not only significantly improve human work efficiency, help people better understand each other through "mind-to-mind communication," but also pave the way for a safer high-intelligence artificial intelligence.
If the infrastructure for biological and health tracking (including at the individual and spatial levels) is based on proprietary technology, then data will default to large corporations. These corporations have the right to develop various applications on the infrastructure, while other entities are excluded. Although they may open partial access through APIs (application programming interfaces), such access is often limited and may be used for "monopolistic rent-seeking," which could be revoked at any time. This means that a few individuals and companies control the core resources of a key technological area of the 21st century, thereby limiting the possibility for other entities to derive economic benefits from it.
On the other hand, if such personal health data lacks security safeguards, once hackers infiltrate, they could exploit health issues for extortion, manipulate insurance and medical product pricing for profit maximization; if the data contains location information, hackers could even stake out and carry out kidnappings based on it. Conversely, your location data (frequently targeted by hacker attacks) could also be used to infer your health condition. And if a brain-machine interface is hacked, it means malicious attackers can directly "read" (or worse—"alter") your thoughts. This is no longer a sci-fi scenario: studies have shown that a brain-machine interface hack could lead to users losing motor control ().
In conclusion, while these technologies can bring tremendous benefits, they also come with significant risks—and emphasizing "openness" and "verifiability" is a key way to mitigate these risks.
The Importance of Openness and Verifiability in the Personal and Business Digital Technology Space
Earlier this month, I needed to fill out and sign a legally binding document, but I was overseas at the time. Although the country had a national electronic signature system, I had not completed the registration in advance. In the end, I had to print the document, sign it by hand, then go to a nearby DHL service point, spend a considerable amount of time filling out a paper courier form, and finally pay to expedite the international shipment of the document. The entire process took half an hour and cost $119. On that same day, I also needed to sign a digital transaction on the Ethereum blockchain—it took only 5 seconds, costing only $0.1 (to be fair, even without relying on the blockchain, digital signatures can be entirely free).
Such cases are very common in scenarios such as corporate or nonprofit organization governance, intellectual property management, and so on. Over the past decade, in the business plans of the vast majority of blockchain startups, one could see similar "efficiency comparison" cases. In addition, the most core application scenario of "exercising individual permissions through digital means" is in the payment and financial field.
Of course, all of this comes with a major risk: what if the software or hardware is subjected to a hacker attack? The cryptocurrency field recognized this risk very early—the blockchain has the characteristics of "permissionless" and "decentralization," so once you lose access to your funds, there is no "savior" to turn to; in other words, "no private key, no asset ownership." It is precisely because of this that the cryptocurrency field began exploring solutions such as "multi-signature wallets," "social recovery wallets," and "hardware wallets" early on. However, in reality, the lack of a "trusted third party" in many scenarios is not due to an ideological choice but rather an inherent attribute of the scenario itself. In fact, even in the traditional financial field, a "trusted third party" can hardly protect the majority of people—for example, only 4% of fraud victims are able to recover their losses. And in scenarios involving "personal data custody," once data is leaked, it fundamentally cannot be "retracted." Therefore, we need true verifiability and security—both in software and ultimately in hardware.
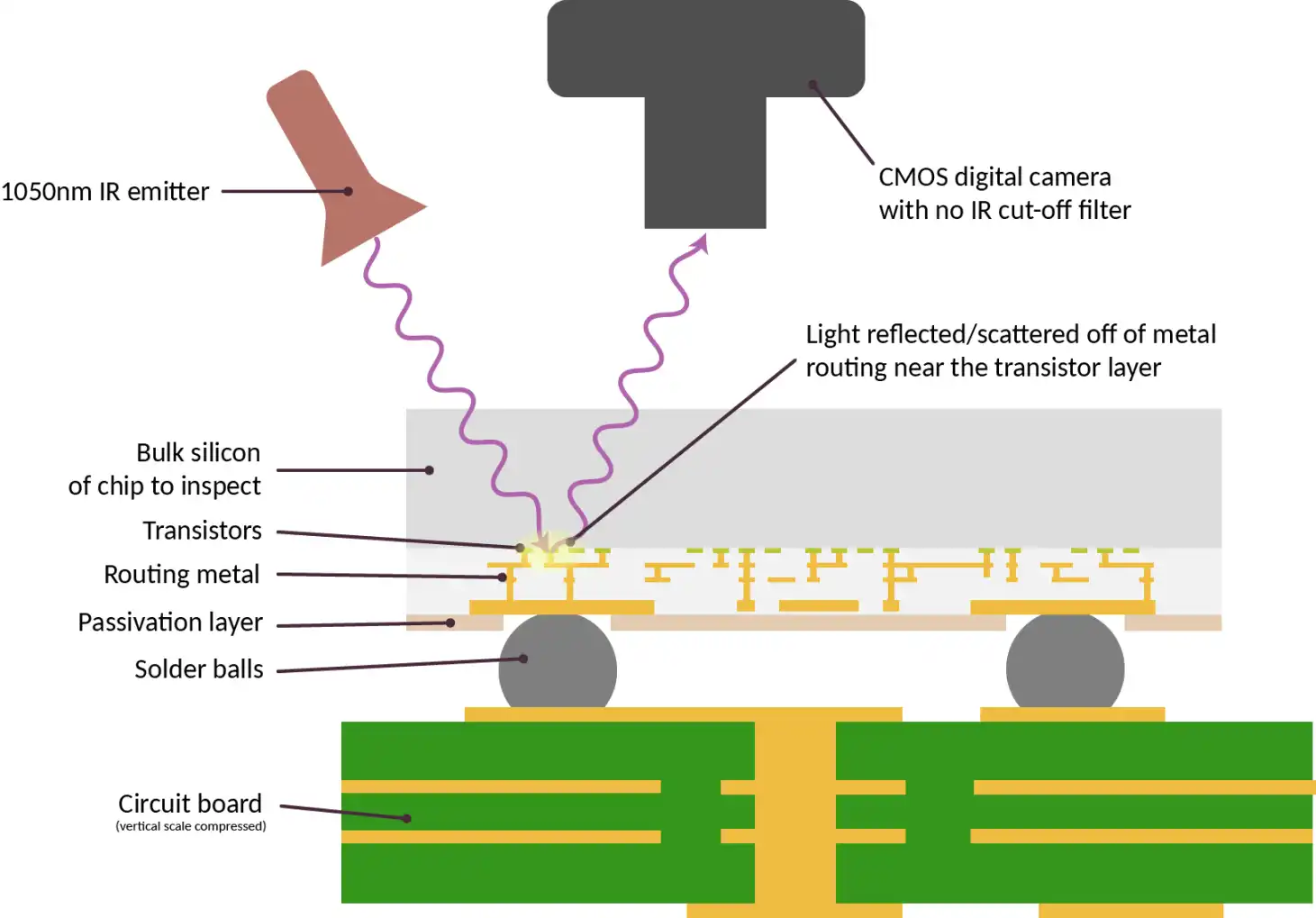
A technology solution for detecting whether computer chip manufacturing is compliant
Importantly, in the hardware field, the risks we are trying to mitigate go far beyond just "whether the manufacturer is malicious." The more core issue is this: hardware development relies on a large number of external components, many of which are in closed-source mode; if any one component has a loophole, it could lead to unacceptable security consequences. Some papers show that even if software is proven "secure" in an isolated model, the choice of microarchitecture may undermine its side-channel resistance. Security vulnerabilities like EUCLEAK (an attack method) are harder to discover precisely because many of the components they rely on are proprietary technologies. In addition, if an artificial intelligence model is trained on compromised hardware, backdoors may be implanted during the training process.
Another issue is this: even if a closed centralized system itself is secure, it brings other downsides. Centralization creates a "persistent power leverage" among individuals, enterprises, or countries—if your core infrastructure is built and maintained by a "potentially untrustworthy enterprise" from a "potentially untrustworthy country," you are susceptible to external pressures (for example, refer to Henry Farrell's research on "weaponized interdependence"). This is exactly the problem that cryptocurrency aims to solve—but the scope of such problems extends far beyond the financial field.
The Importance of Openness and Verifiability in the Digital Citizenship Technology Field
I often engage with people from various industries who are exploring government governance models more suitable for the 21st century's different scenarios. For example, Audrey Tang is dedicated to upgrading the existing functional political system by empowering local open-source communities and adopting mechanisms such as "citizen councils," "sortition representation," and "second-round voting" to enhance governance quality. Some others start from the "bottom-up design" — some Russian-born political scientists have drafted a new constitution for Russia, which explicitly guarantees individual freedom and local autonomy, emphasizes institutional design of "a tendency for peace, opposition to aggression," and gives unprecedented importance to direct democracy. There are also scholars (such as economists studying land value tax or congestion charge) working to improve their country's economic situation.
While different people may have varying degrees of acceptance of these ideas, they all share a common point: they all require "high-bandwidth participation," so any practical implementation must be digital. Paper-based records may suffice for "simple property registration" or "once-in-four-years elections," but they are completely inadequate for scenarios requiring higher participation frequency and information transmission efficiency.
However, historically, security researchers' attitudes towards digital citizenship technologies such as "electronic voting" have ranged from skepticism to opposition. Some research has nicely summarized the core reasons for opposing electronic voting, mentioning:
"First, electronic voting technology relies on 'black-box software' — the public cannot access the voting machine's software code. Although companies claim that 'protecting software is to prevent fraud, counter competition,' this also leads to the public being completely unable to understand the voting software's operational logic. If a company wants to manipulate the software, create false election results, it is not difficult. Additionally, there is a competitive relationship between voting machine suppliers, and there is no guarantee that they will produce equipment based on 'voter interests' and 'ballot accuracy'."
A plethora of real-world cases proves that this skepticism is not unfounded.
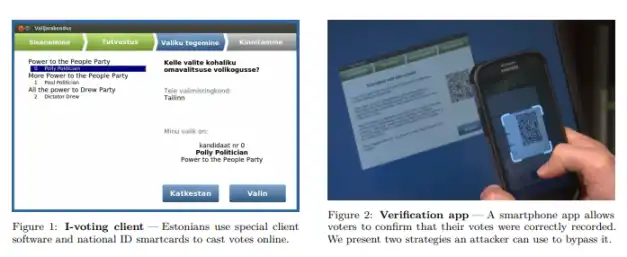
Critical Analysis of Estonia's Internet Voting System in 2014
These opposition reasons also apply to similar scenarios. However, I predict that with technological advancements, in more and more fields, the attitude of "completely rejecting digitization" will become increasingly unrealistic. Technology is driving the world towards higher efficiency development (regardless of pros and cons). If a system rejects to follow this trend, people will gradually bypass it to conduct activities, and its influence in personal and collective affairs will continue to weaken. Therefore, we need another solution: face the challenges and explore how to make complex technological solutions have "security" and "verifiability."
In theory, "Secure Verifiability" and "Open Source" are two different concepts. Proprietary technology could indeed have security — for example, aircraft technology is highly proprietary, yet commercial aviation remains a very secure mode of transportation. However, what a proprietary model cannot achieve is "secure consensus" — the ability to have security recognized by mutually untrusting parties.
Electoral systems and other civic systems are typical scenarios that require "secure consensus." Another scenario is evidence collection in a courtroom. Recently, a Massachusetts court in the United States ruled that a large number of breathalyzer test results were invalid — the reason being that the state crime lab was found to have concealed information about widespread failures of the breathalyzers. The ruling document stated:
"Are all the test results flawed? No. In fact, most of the breathalyzers in question did not have calibration problems. But investigators later found that the state crime lab had concealed evidence that the 'scope of the failures was wider than the lab had acknowledged,' leading Judge Frank Gaziano to conclude that the due process rights of all the relevant defendants were violated."
In the courtroom, "due process" essentially demands not just "fairness" and "accuracy," but also "fair and accurate consensus" — if the public cannot confirm that the court is "acting within the law," society is likely to descend into a state of "self-help" chaos.
Furthermore, "openness" itself holds inherent value. Openness allows local communities to design governance, identity verification, and other systems tailored to their goals. If a voting system relies on proprietary technology, a country (or state, or city) wishing to try a new voting method would face significant barriers: either convincing a company to develop their preferred rules as a "new feature," or starting from scratch to develop and secure verification — undoubtedly greatly increasing the cost of political system innovation.
In these domains, adopting the "open-source hacker ethic" (which encourages sharing, collaboration, and innovation) can empower local implementers, whether they are acting as individuals or as part of a government or a company. To achieve this, two conditions must be met: widespread availability of "easy-to-build open-source tools" and infrastructure and code repositories adopting a "free license" model, allowing others to build upon them. If the goal is to "reduce power differentials," then the "copyleft" mode is particularly important.

In the coming years, another important direction in civic technology will be physical security. Over the past two decades, surveillance cameras have been ubiquitous, raising many concerns about civil liberties. Unfortunately, the rise of drone warfare has made "not adopting high-tech security measures" no longer a viable option. Even if a country's laws do not infringe on civil liberties, if that country cannot protect its citizens from "other countries (or malicious enterprises, individuals)" engaging in illegal interference, the so-called "freedom" becomes a moot point — and drones have made such attacks easier. Therefore, we need appropriate defense measures, which may include a large number of "anti-drone systems," sensors, and cameras.
If these tools are proprietary, data collection will be both opaque and highly centralized; if these tools have both "openness" and "verifiability," we can explore a better solution: secure devices will only output limited data in limited scenarios and will automatically delete the rest of the data. In this way, the future of digital physical security will be more like a "digital watchdog" than a "digital panoptic prison." We can envision a world where public surveillance devices must be open source and verifiable, where any citizen has the legal right to "randomly select public surveillance devices, dismantle and verify their compliance," and even university computer clubs can use this verification as a teaching practice.
Open Source and Verifiable Implementation Path
We cannot avoid the deep integration of digital computing technology into all aspects of individual and collective life. If left unchecked, the future of digital technology is likely to take the form where it is developed and operated by centralized corporations serving the profit motives of a few, implanted with backdoors by national governments, and where the majority of people globally are unable to participate in technology creation or assess its security. However, we can strive to take a better path.
Imagine this world:
· You have a secure personal electronic device—it combines the computing power of a smartphone with the security of an encrypted hardware wallet, with a level of inspectability not as good as a mechanical watch but already very close.
· All your instant messaging applications are encrypted, message transmission paths are hidden using mixnet technology, and all code has undergone formal verification.
· You can be completely sure that private conversations are truly confidential.
· Your financial assets are in on-chain standardized ERC-20 tokens (or stored in servers that publish hashes to the blockchain along with proofs of validation for accuracy), managed by a wallet controlled by your personal electronic device.
· If the device is lost, you can recover asset access through a self-selected method (such as combining your other devices, family, friends, or institution devices—not necessarily government institutions: if the operation is convenient enough, organizations like churches may also provide such services).
· An open-source version of Starlink-level infrastructure is in use, ensuring global communication is stable and reliable without relying on a few operating entities.
· Your device is equipped with a locally run open-source weighty large language model (LLM) that can scan your operations in real time, provide suggestions, automate tasks, and issue warnings when you may receive incorrect information or are about to make a mistake.
· The device's operating system is also open source and has undergone formal verification.
· You wear a 24/7 personal health tracking device that operates continuously, providing you with open-source access and verifiability of your health data. You can access your health information at any time and ensure that no one can access this information without your permission.
· We have a more advanced governance model: employing mechanisms such as sortition representation, citizen assemblies, and second-round voting, we set goals through a cleverly designed democratic voting process and select expert solutions to achieve these goals.
· As a participant, you can be confident that the system is operating according to your understanding of the rules. Public spaces are equipped with monitoring devices for tracking biometric variables (such as monitoring CO2 levels, air quality index, airborne disease presence, wastewater indicators, etc.).
· However, these devices (along with all surveillance cameras and defensive drones) feature openness and verifiability, supported by a corresponding legal framework that allows the public to conduct random checks.
In such a world, we will have higher security, more freedom, and a more equitable opportunity for global economic participation than we currently do. However, to achieve this vision, increased investment is needed in the following technological areas:
· Advanced Encryption Technology: I refer to technologies such as Zero-Knowledge Proofs (ZK-SNARKs), Fully Homomorphic Encryption, and Obfuscation as the "Egyptian God Cards" of the encryption field—they excel at performing arbitrary computations on data in multi-party scenarios, ensuring the reliability of output results while preserving the privacy of data and computation processes. This lays the foundation for developing more robust privacy-preserving applications. Tools related to encryption (such as blockchain, which ensures data integrity and user inclusion, and differential privacy technology, which enhances privacy by adding noise to data) will also play a crucial role here.
· Application and User-Level Security: True security of an application exists only when the security commitments of the application are understandable and verifiable by the user. This requires leveraging software frameworks to reduce the development complexity of high-security applications. Furthermore, browsers, operating systems, and other middleware (such as locally running monitoring large-scale language models) need to work together to validate the security of applications, assess risk levels, and clearly present this information to users.
· Formal Verification: We can utilize automated proof methods to algorithmically verify if programs satisfy key properties (such as data non-disclosure and prevention of unauthorized third-party modifications). Lean language has recently become a popular tool in this field. Currently, these technologies have begun to be used to verify zero-knowledge proof algorithms of the Ethereum Virtual Machine (EVM) and other high-value, high-risk use cases in the encryption field, with similar applications in broader fields. Additionally, further breakthroughs are needed in other more fundamental security practices.
The fatalistic view at the beginning of the 21st century that "cybersecurity is incurable" is incorrect: vulnerabilities (and backdoors) are not insurmountable. We "just need" to learn how to prioritize security above other competitive objectives.
· Open Source and Security-Centric Operating Systems: These systems are continually emerging, such as the security-focused Android derivative GrapheneOS, kernels that emphasize minimal security (such as Asterinas), and Huawei's HarmonyOS—HarmonyOS has an open-source version and is adopting formal verification technology. Many readers may question: "Since it's Huawei's system, there must be backdoors, right?" However, this view precisely overlooks a core logic: regardless of the product's developer, as long as it is open and anyone can verify it, the developer's identity should not be a concern. This case fully demonstrates that openness and verifiability can effectively counteract the global trend of technological fragmentation.
· Secure Open Source Hardware: If hardware cannot ensure that it is genuinely running the specified software and will not clandestinely leak data in the background, then even the most secure software is meaningless. In this field, I focus on two short-term goals:
a. Personal Secure Electronic Devices: Referred to as "hardware wallets" in the blockchain field and as "secure phones" by open-source enthusiasts—but as long as the dual requirements of "security" and "usability" are understood, the core functions of these two types of devices will ultimately converge.
b. Public Physical Infrastructure: This includes smart locks, the aforementioned biometric monitoring devices, and various IoT technologies. To earn public trust in such facilities, openness and verifiability are essential prerequisites.
· Secure Open Source Toolchain for Building Open Source Hardware: Today, hardware design relies heavily on closed-source components. This not only significantly raises hardware R&D costs and increases the development permission threshold but also makes hardware verification difficult to implement—if the tools for generating chip designs are closed-source, developers cannot determine verification standards. Even existing technologies like scan chains often cannot be practically applied due to critical proprietary tools. However, this situation is not insurmountable.
· Hardware Verification Technologies (such as IRIS technology, X-ray scanning): We need to scan chips to confirm that their logic matches the design completely and that there are no additional components that could be maliciously tampered with to extract data. Verification can be achieved in two ways:
a. Destructive Verification: Auditors, posing as regular end-users, randomly purchase products containing chips, dismantle the chips, and verify whether their logic matches the design.
b. Non-destructive Verification: Using IRIS or X-ray scanning technology, it is theoretically possible to inspect each individual chip.
In order to achieve "Security Consensus," the ideal state is for a large group of people to be able to grasp hardware verification technology. Currently, X-ray equipment is not yet widespread, but this can be improved in two ways: on one hand, by optimizing verification equipment (and designing chips for verifiability), lowering the barrier to entry; on the other hand, by supplementing "full verification" with simpler verification methods — such as ID tag verification that can be done on a smartphone, signature verification based on physically unclonable function-generated keys. These methods can effectively verify key information such as "whether the device comes from a known manufacturer batch, and whether that batch has been rigorously verified through third-party random sampling."
· Open-source, low-cost local environment and biometric monitoring devices: Communities and individuals should be able to independently monitor the environment and their own health, identifying biological risks. These devices come in various forms, including personal medical devices like OpenWater, air quality sensors, general air-transmitted disease sensors like Varro, and larger-scale environmental monitoring devices.
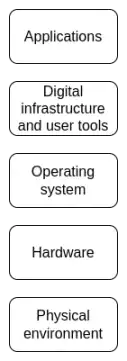
Every layer of the technology stack needs to be open and verifiable.
From Vision to Implementation: Path and Challenges
Compared to the traditional vision of technological development, the key difference in the vision of "Full-stack Open-source Verifiability" is that it places more emphasis on safeguarding local sovereignty, empowering individual rights, and achieving freedom. In terms of secure construction logic, it no longer seeks to "completely eliminate all global threats," but shifts towards "enhancing the robustness of systems at every level of the tech stack"; in the definition of "openness," it goes beyond "centrally planned API open access" to extend to "improvement, optimization, and secondary development of every layer of the technology stack"; in terms of "verification," it is no longer the exclusive power of proprietary auditing agencies (which may even collude with tech companies or governments), but becomes a fundamental right of the public, and even a socially encouraged practice — where anyone can participate in verification, rather than passively accepting "security assurances."
This vision is more adaptable to the fragmented global landscape of the 21st century, but the window for implementation is very tight. Currently, centralized security solutions are advancing at an alarming rate, their core logic being "increasing centralized data collection nodes, pre-installing backdoors, while simplifying verification into a single standard — 'whether it comes from a trusted developer or manufacturer'." In fact, attempts to replace "truly open access" with centralized solutions have never stopped for decades: from Facebook's early "Internet.org" initiative to today's more complex technological monopoly models, each attempt is more deceptive than the last. Therefore, we face a dual task: on one hand, to accelerate the research and implementation of open-source verifiable technology to compete with centralized solutions; on the other hand, to clearly convey the idea to the public and institutions that "a safer, fairer technological solution is not a pipe dream, but a tangible reality."
If we can achieve this vision, we will usher in a world that can be called "Retrofuturism": on one hand, we can enjoy the benefits of cutting-edge technology—improving health with more powerful tools, organizing society in a more efficient and robust manner, and defending against new and old threats (such as pandemics and drone attacks); on the other hand, we can rediscover the core traits of the 1900s technology ecosystem—where infrastructure is no longer a "black box inaccessible to ordinary people" but a tool that can be dismantled, verified, and reconfigured to fit one's own needs; anyone can break through the identity limits of "consumer" or "app developer" and participate in innovation at any layer of the technology stack (whether optimizing chip design or enhancing operating system security logic); more importantly, people can truly trust the technology—ensuring that the device's actual functionality aligns with its promotion, does not steal data in the background, or perform unauthorized operations.
Realizing "Full-Stack Open Source Verifiability" is not without cost—performance optimization of software and hardware often comes at the expense of "reduced comprehensibility and increased system vulnerability," and the open-source model is also in conflict with most traditional commercial profit logic. Although the impact of these issues is exaggerated, the public and market's shift in perception towards "open-source verifiability" takes time and cannot be achieved overnight. Therefore, we need to set a clear short-term goal: prioritize building a full-stack open-source verifiability technology system for "high-security-demand, rather than performance-critical applications," covering consumer and institutional scenarios, remote and local scenarios, as well as software, hardware, and biometric monitoring domains.
The rationale for this choice is as follows: in most scenarios with extremely high requirements for "security" (such as health data storage, election voting systems, financial key management), the demand for "performance" is not actually stringent; even in scenarios where some performance is required, a balance can be achieved through a combination strategy of "high-performance untrusted components + low-performance trusted components"—for example, using a high-performance chip to process ordinary data and using an open-source verified secure chip to handle sensitive information, ultimately meeting efficiency needs while ensuring security.
We do not have to pursue "utmost security and openness in all areas"—this is neither realistic nor necessary. But we must ensure that in those core areas directly related to individual rights, social equity, and public safety (such as healthcare, democratic participation, and financial security), "open-source verifiability" becomes a technological standard, allowing everyone to enjoy secure and trustworthy digital services.
A special thanks to Ahmed Ghappour, bunnie, Daniel Genkin, Graham Liu, Michael Gao, mlsudo, Tim Ansell, Quintus Kilbourn, Tina Zhen, Balvi volunteers, and GrapheneOS developers for their feedback and participation in the discussions.
Disclaimer: The content of this article solely reflects the author's opinion and does not represent the platform in any capacity. This article is not intended to serve as a reference for making investment decisions.
You may also like
Bitget donates HK$12 million to support fire rescue and reconstruction efforts in Tai Po, Hong Kong
Bitget Spot Margin Announcement on Suspension of ELX/USDT Margin Trading Services
Enjoy perks for new grid traders and receive dual rewards totaling 150 USDT
Bitget Spot Margin Announcement on Suspension of BEAM/USDT, ZEREBRO/USDT, AVAIL/USDT, HIPPO/USDT, ORBS/USDT Margin Trading Services
