What is EtherHiding? Google flags malware with crypto-stealing code in smart contracts
North Korean hackers have adopted a method of deploying malware designed to steal crypto and sensitive information by embedding malicious code into smart contracts on public blockchain networks, according to Google’s Threat Intelligence Group.
The technique, called “EtherHiding,” emerged in 2023 and is typically used in conjunction with social engineering techniques, such as reaching out to victims with fake employment offers and high-profile interviews, directing users to malicious websites or links, according to Google.
Hackers will take control of a legitimate website address through a Loader Script and embed JavaScript code into the website, triggering a separate malicious code package in a smart contract designed to steal funds and data once the user interacts with the compromised site.
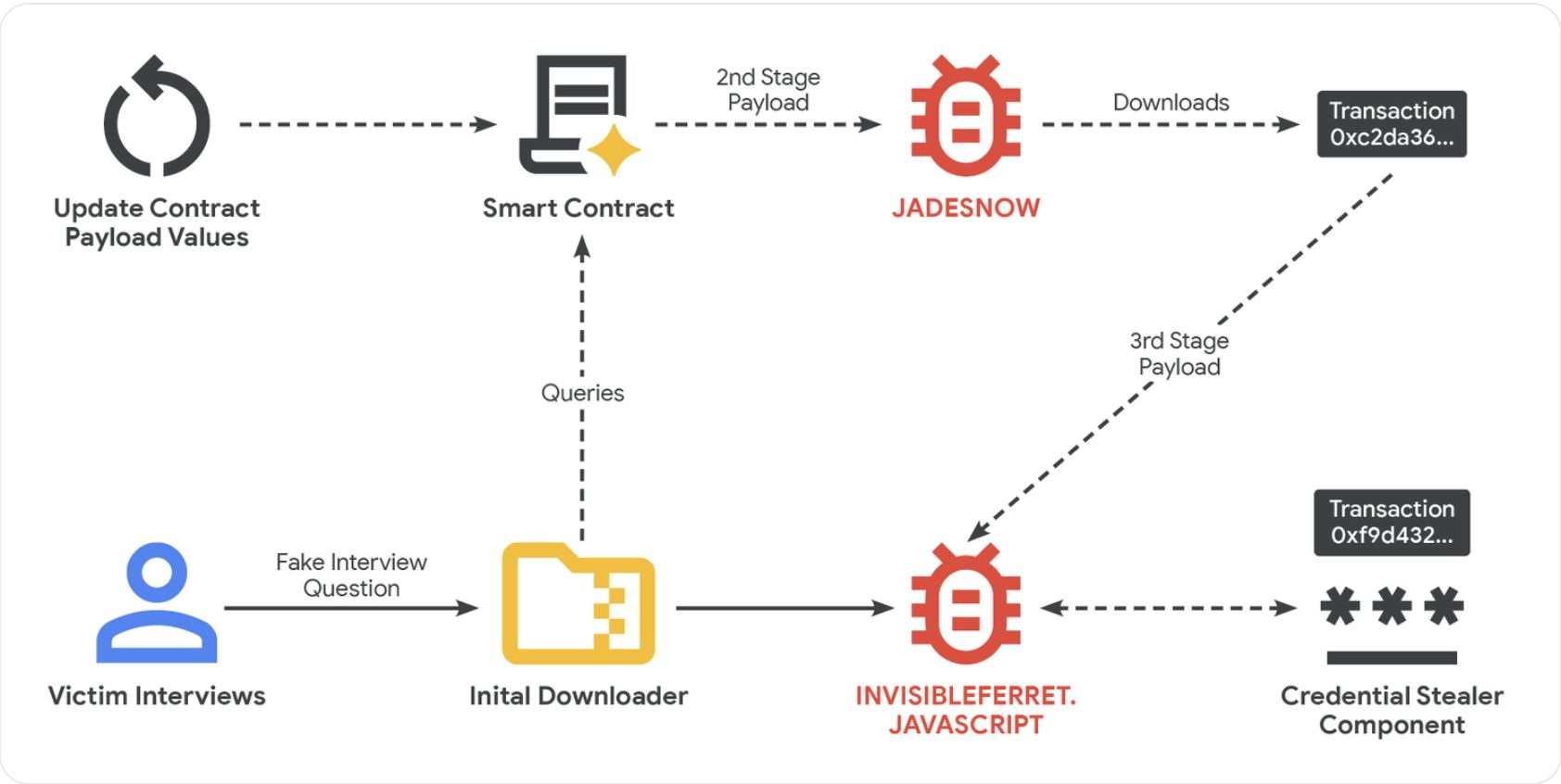
The compromised website will communicate with the blockchain network using a “read-only” function that does not actually create a transaction on the ledger, allowing the threat actors to avoid detection and minimize transaction fees, Google researchers said.
The report highlights the need for vigilance in the crypto community to keep users safe from scams and hacks commonly employed by threat actors attempting to steal funds and valuable information from individuals and organizations alike.
Related: CZ’s Google account targeted by ‘government-backed’ hackers
Know the signs: North Korea social engineering campaign decoded
The threat actors will set up fake companies, recruitment agencies and profiles to target software and cryptocurrency developers with fake employment offers, according to Google.
After the initial pitch, the attackers move the communication to messaging platforms like Discord or Telegram and direct the victim to take an employment test or complete a coding task.
“The core of the attack occurs during a technical assessment phase,” Google Threat Intelligence said. During this phase, the victim is typically told to download malicious files from online code repositories like GitHub, where the malicious payload is stored.
In other instances, the attackers lure the victim into a video call, where a fake error message is displayed to the user, prompting them to download a patch to fix the error. This software patch also contains malicious code.
Once the malicious software is installed on a machine, second-stage JavaScript-based malware called “JADESNOW” is deployed to steal sensitive data.
A third stage is sometimes deployed for high-value targets, allowing the attackers long-term access to a compromised machine and other systems connected to its network, Google warned.
Magazine: Inside a 30,000 phone bot farm stealing crypto airdrops from real users
Disclaimer: The content of this article solely reflects the author's opinion and does not represent the platform in any capacity. This article is not intended to serve as a reference for making investment decisions.
You may also like
Evaluating How Vitalik Buterin's Advancements in ZK Technology Are Shaping Blockchain Investment Trends
- Vitalik Buterin's GKR protocol boosts Ethereum's scalability, enabling 43,000 TPS via ZK computation. - Institutional adoption accelerates with ZK-based compliance solutions, attracting BlackRock and Deutsche Bank partnerships. - ZK startups like zkSync and StarkNet secure $55M+ in funding, with market caps surging as infrastructure matures. - Investors target ZK-EVM compatible projects and hybrid models, aligning with Ethereum's 2026 roadmap.

ZK Technology's 2025 Price Increase: Sustained Value Driven by Blockchain Integration and Growing Institutional Engagement
- ZK technology's 2025 price surge stems from on-chain adoption and institutional investments, signaling a structural market shift. - ZK rollups now process 15,000 TPS with $3.3B TVL, driven by infrastructure upgrades and 230% developer engagement growth. - 35+ institutions including Goldman Sachs deploy ZKsync for confidential transactions, while Nike/Sony adopt it for supply-chain transparency. - Market fundamentals project 22.1% CAGR to $7.59B by 2033, validating ZK as blockchain's foundational infrastr

DASH Experiences 150% Price Jump and Growing Institutional Interest: Examining Blockchain’s Strength During Economic Uncertainty
- DASH surged 150% in June 2025 driven by tech upgrades, institutional interest, and favorable policies. - Platform 2.0 enhanced scalability and token support, positioning DASH as a competitive blockchain platform. - Institutional adoption grew in 2025 Q3-Q4 via merchant integrations in emerging markets and decentralized governance. - Macroeconomic factors like Fed policies and M2 growth boosted liquidity, while volatility persisted due to tightening markets. - Future growth depends on 2026 regulatory clar
The Increasing Importance of Stablecoins in Institutional Investment Strategies
- In 2025, U.S. GENIUS Act and EU MiCA regulations drove institutional adoption of USDC as a compliant, transparent stablecoin. - USDC's 98% U.S. Treasury-backed reserves and monthly audits made it preferred over USDT for regulated entities. - Institutions used USDC to reduce settlement delays by 35% and improve Sharpe ratios by 12% through yield-generating strategies. - With $73.7B circulation and $140B Q3 transaction volume, USDC became a 24/7 global liquidity tool for emerging markets.

