Technology in the blockchain world is changing rapidly, but the best tools are probably just a couple of clicks away from being installed on your smartphone. The best crypto wallets of 2026 are already available today. Not the ones that will appear tomorrow, but the ones that are already showing what secure and convenient storage looks like. Including BTC, USDT.
We have selected six wallets that are already setting the standard that the rest of the industry can only aspire to. And in 2026, their leadership will remain unchanged.
- Trustee Plus.
Truste Plus is a non-custodial service for managing digital assets with built-in P2P and cryptocard – in the ranking by Incrypted, the largest crypto media outlet in Eastern Europe, Trustee topped the list of the TOP 12 crypto cards .

Transfers within the wallet are instant and made with 0% commission – by phone number and IBAN (international bank account number). Stablecoin exchange is also 0%. The development team, led by Vadim Grusha , has been operating since 2017.
Despite being non-custodial, the service uses cryptographic methods to protect your funds. To do this, it encrypts the connection between the user and the server, the connection signature, and the data at the moment of transmission and storage, using anonymisation and access via separate requests. It is based on modern protocols such as AES-256 (also DES), Transport Layer Security (TLS), Rivest-Shamir-Adleman, and ECC.
Wallet security is important in two ways. To this end, the service offers to set up an account with a PIN, biometrics (TouchID or FaceID) and two-factor authentication via email and Google Authenticator. A PIN is not just a password, but part of the encryption. It is used to encrypt the signature, and the PIN and biometrics are used to encrypt the authorization key.
- Ledger.

One of the oldest hardware wallets on the market, rightly considered a secure way to store cryptocurrencies. Ledger devices store access keys offline and only connect to the network when in use. The key is protected by a special chip certified to CC EAL5+ and EAL6+ standards.
- Metamask.
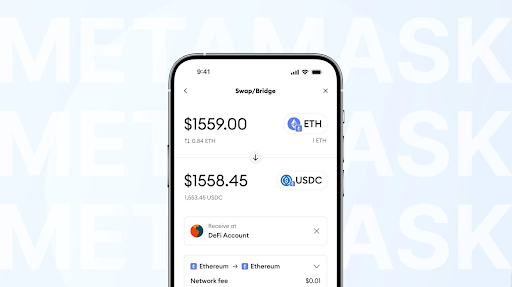
A crypto wallet with one of the largest user bases in the world, focused on working with Ethereum and L2. It supports ETH and ERC-20 tokens, which will allow you to store USDT in this format, but will not allow you to work with Bitcoin.
As a custodial wallet, Metamask stores each wallet’s unique key on the user’s device – the key never leaves the device, ensuring security. This means that no server stores the key, making recovery impossible if lost. As an additional measure, it offers alerts about phishing.
- Trezor.

Another hardware wallet that has been on the market since 2013. It supports over 8,000 currencies, including BTC and USDT. In addition to hardware storage measures, Trezor offers manual confirmation of each transaction on the device screen, which protects against address spoofing. All operations are signed internally, and the keys are isolated, which protects even if the device is infected with a virus.
- Trustee Wallet.
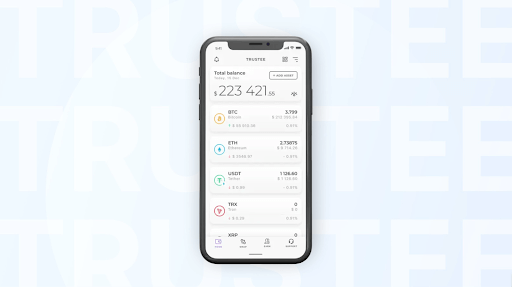
Another crypto wallet from the Trustee team, operating on the market since 2019. Unlike Plus, this is a custodial service, i.e. an application that stores access keys to assets on the blockchain only on the user’s device. The key is encrypted using AES and other algorithms, and the developers are constantly working to improve security, taking into account current technological threats.
- OKX Wallet.
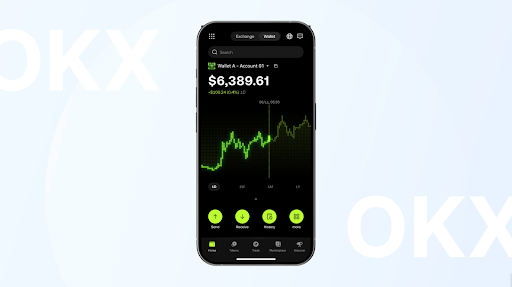
A decentralised wallet from the OKX crypto exchange that operates independently of it. Account balances are not linked, but transfers between platforms are simplified. The wallet allows you to create up to 1,000 sub-accounts for BTC and USDT and hundreds of other currencies at the same time, with each key on the user’s side. Plus, it offers proactive protection against malicious domains and smart contracts, and guarantees regular wallet checks by cybersecurity experts.
Hardware and custodial wallets remain the gold standard for security, protecting assets through cold storage and key isolation. However, using them requires experience and attention to detail. Today, a new generation of solutions is emerging – they combine the level of hardware devices with the simplicity of mobile applications, making control over crypto accessible to everyone – without compromise.
They build 100% security, but allow you to tailor it to your needs – from key management to additional levels of protection and access recovery.